The December 2020 cyber-attack on the information technology monitoring and management company SolarWinds’ Orion platform, used by governments and corporations, has once again brought forth the vulnerabilities of an interconnected world. The U.S. Computer Emergency Response Team (U.S. CERT) has released an emergency directive to tech companies and government agencies to unplug from the Orion platform immediately.[1]
Cyber-attacks pose a greater threat to industries like manufacturing and energy than to software or service-based companies. The realm of cyber-physical systems allows the cyberworld to manipulate the physical. The Ukraine power grid crisis,[2] the Stuxnet attack, the Saudi Aramco[3] attack had all resulted in crippled systems, not only causing business loss but also endangering lives.
A compromised electric system can cause fire safety issues in the office premises. A compromised safety system in a manufacturing plant is a threat to all employees. A compromised safety system in a nuclear power plant can be a threat to an entire city.
Thus, the threat spectrum in the era of industrial internet of things moves from just data security, intellectual property theft, and industrial espionage to the security of physical assets such as machinery to the safety and security of people.
The table below lists industrial cyber-attacks in the last decade.
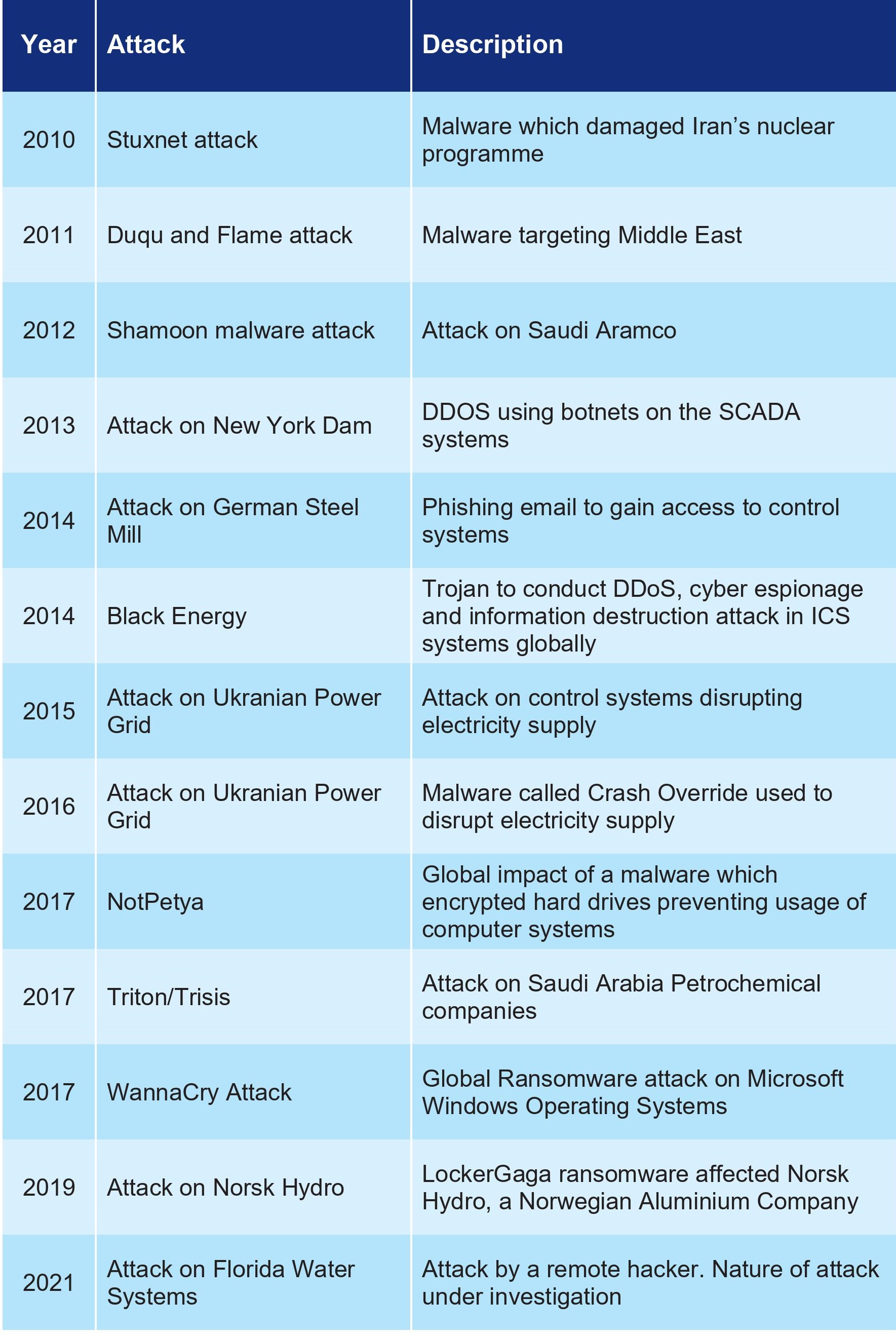
Source: Gateway House Research, US CERT, ISA/IEC 62443 Guidebook
Industrial Cybersecurity can be divided into two parts: Information Technology (IT) security and Operations Technology (OT) security. Operations Technology is defined as hardware and software used to control industrial assets. It includes Industrial Control Systems (ICS), supervisory control and data acquisition (SCADA) systems, and Programmable Logic Controllers (PLC) which provide an interface between the virtual and physical worlds.
As per IBM’s Threat Intelligence Index report 2020, attacks on Operational Technology saw a 2000% year on year increase in 2019. Though cybersecurity in IT systems have matured over the ages, applying only IT solutions in industries will not provide 360-degree security. This is because the primary goal of IT security is to protect information while the primary goal of OT security is to protect physical assets and people.
Traditionally, OT systems were not connected to the internet – which helped with immunity to cyberattacks that the IT industry encountered. The drive to digitise and connect everything brought with it the additional risk of cyber-attacks. With the current digitisation blitz, industrial systems are getting connected to the world wide web at an unprecedented rate. Juniper Research predicts that the total number of Industrial IoT connections will reach 36.8 billion by 2025.[4] It is difficult for security providers to match this speed.
Malware and ransomware are the major attack vectors.[5] Stuxnet, NotPetya, and LockGrid were all malware. The 2019 attack on Norwegian Aluminium company, Norsk Hydro, was through the LockGrid ransomware which caused an estimated damage of $75 million.[6]
Amongst other challenges, legacy operating systems[7] which are not supported by software providers are a major concern. These systems run on workarounds, as there are no security patches available for old operating systems. It is imperative that migration of legacy systems to newer IT solutions is done quickly to counter modern day cyber-attacks.
The nature of attack changes with industrial internet of things. For instance, a distributed denial of service (DDoS) attack on an IT system will only prevent users from availing of a service. However, a DDoS attack on a temperature control system may cause overheating and a breakdown of machinery. Thus, the surface area of attack is more and the ability to cause physical damage is vast. Organisations must apply existing IT security solutions to their processes. For example, updating software with the latest patches, firewalls to protect the companies’ networks, and whitelisting and access control to ensure only authenticated individuals can operate a machine are some of the measures to be implemented.
Apart from IT security solutions, OT requires additional security. A cyber-physical system requires both software and hardware solutions. IT provides software solutions; however, software tends to have bugs and vulnerabilities. So, to ensure depth in defence, hardware security solutions need to complement software. Air gaps and Unidirectional hardware gateways are two solutions that can increase security exponentially.[8]
- Air gaps:[9] These are isolated networks where critical infrastructure is physically segregated from the corporate network. Air gaps disallow systems like Wi-Fi and allow only specific modes of network communication. Insider threats – such as malicious USB ports – pose a major risk to air gapped systems. The success of the Stuxnet attack on an air gapped Iranian nuclear facility was allegedly due to an insider attack.[10]
- Unidirectional hardware gateways:[11] This equipment allows network traffic to flow in only one direction and is physically unable to send any information at all back into the source network. For instance, data captured through sensors on a factory floor and stored on servers can be prevented from external access through a unidirectional hardware gateway. Any analysis or data access requests can be fulfilled by replicating the data on a different server which can be accessed by external IT systems. This prevents any attacker trying to get in the system as the gateway blocks all incoming traffic.
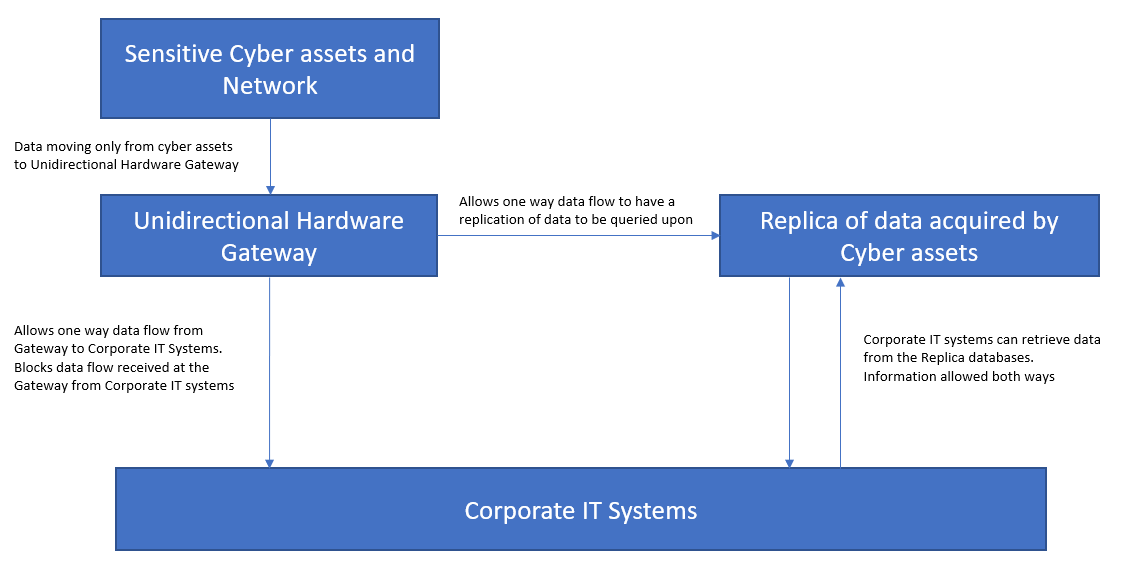
Source: Gateway House Research, NIST SP 800-82 Rev. 2
It must be noted that whatever measures are implemented in an existing system, they have to be first run in a test bed or sandbox, simulating a real-life attack scenario before being applied in a production environment. Security measures can be administered only after thorough penetration testing.
Such measures and other strategies can be found in two guiding documents for industrial cybersecurity: a framework by U.S. government’s National Institute of Standards & Technology (NIST) and a standard by International Society of Automation (ISA) & International Electrotechnical Commission (IEC).
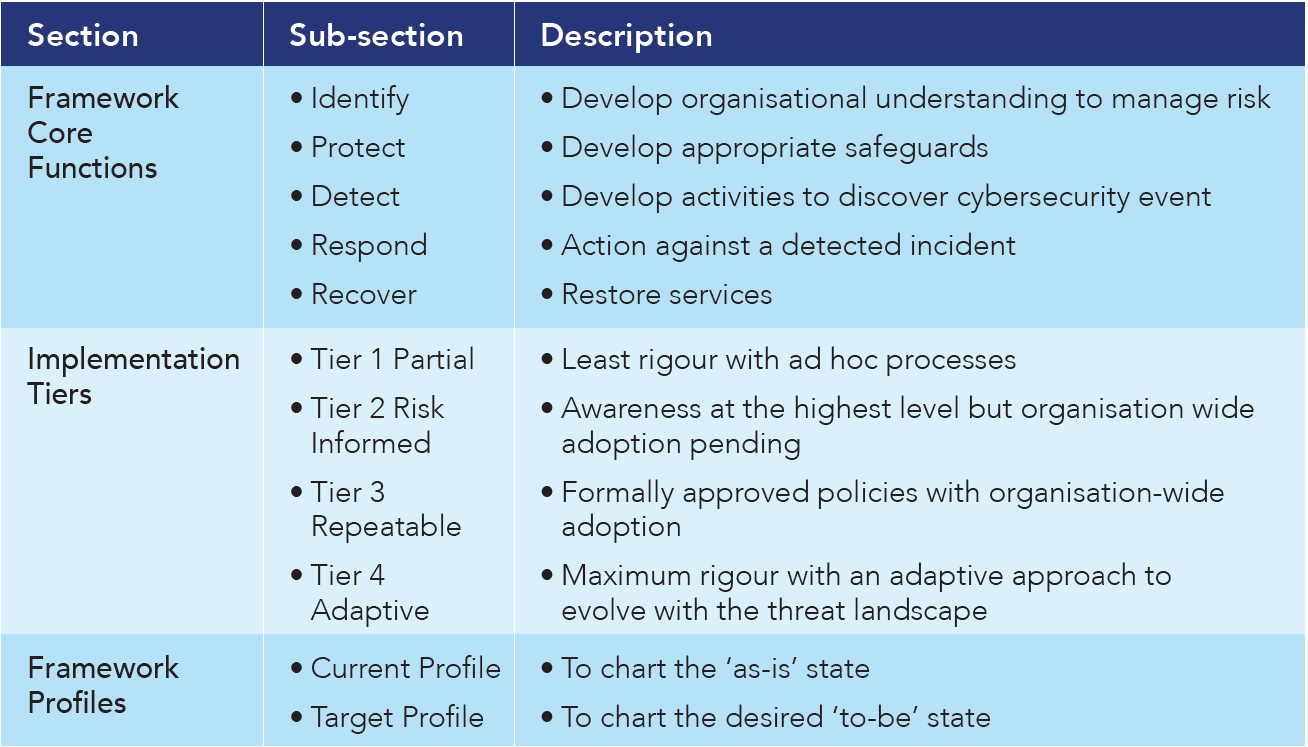
- NIST Cyber framework for Improving Cybersecurity of Critical infrastructure:[13] The framework helps in categorising risks into various buckets with corresponding standards that may apply. The framework is divided into three sections:
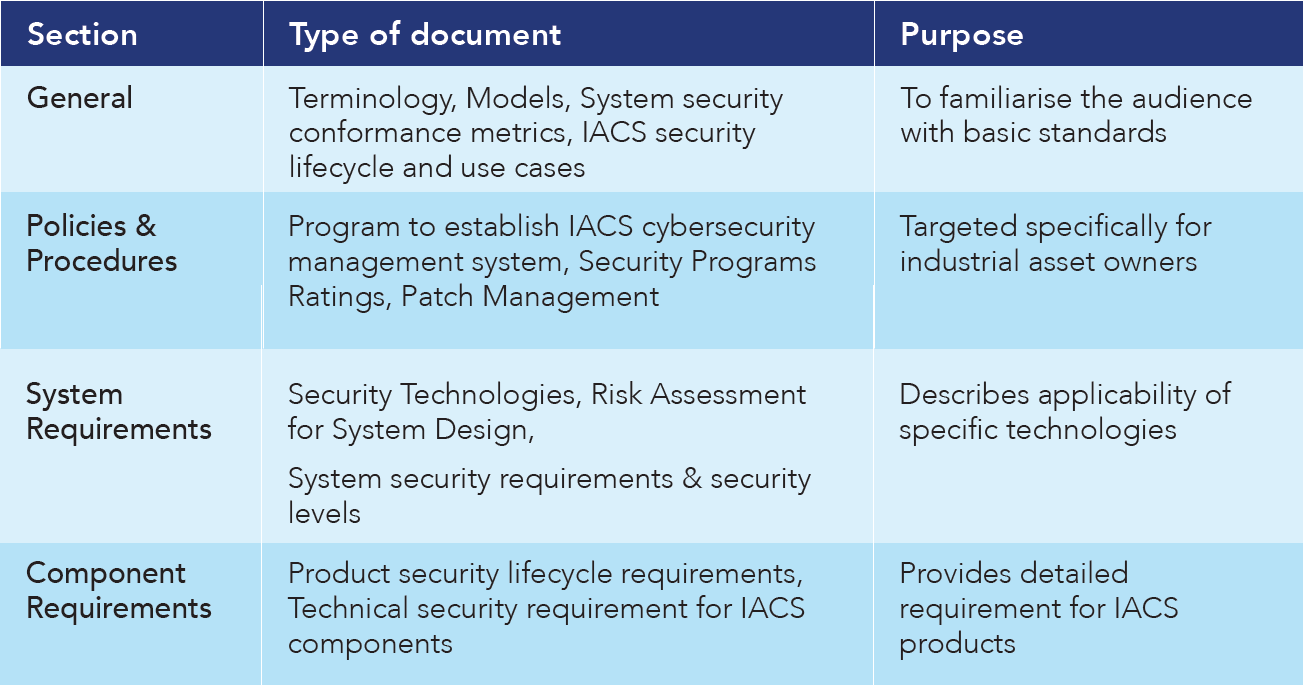
- ISA/IEC 62443[14] – The International Society of Automation and International Electrotechnical Commission have jointly produced the ISA/IEC 62443 standard for security of Industrial Automation and Control Systems (IACS). IACS is defined by this standard as “a collection of personnel, hardware, software, and policies involved in the operation of the industrial process and that can affect or influence its safe, secure and reliable operation”.[15] OT systems are covered by this standard. The standard highlights that extending purely IT security solutions to industrial cybersecurity will not provide a comprehensive security solution. The ISA/IEC 62443 family of standards is divided into four sections:
Despite applying all standards and taking maximum precautions, a system may still be penetrated. Therefore, standard operating procedures (SOPs) should exist for not only what needs to be done before an attack, but also during and after an attack. An end-to-end incident response mechanism can minimise damage during a crisis. After an attack has been contained, special attention needs to be given to recovery. The Mean Time to Recover (MTTR) in IT systems is quite minimal, but industrial systems could take much longer to recover. An IT system can be restored fairly quickly with previous data and system backups. However, an attack that has led to, for example, shutting a furnace in a steel plant, can cause heavy business losses and recovery could take months.
The following recommendations can help mitigate industrial cyber risks:
1. Physical protection along with IT protection: Software security solutions alone cannot protect physical assets and machinery. Integrated software and hardware protection are needed for maximum protection.
2. Security Drills: Cybersecurity attack and response drills help an organisation to manage attacks. Appropriate response protocols prevent sudden panic and help to contain an attack.
3. An integrated Chief of IT & OT: Chief Information Officer and Chief Information Security Officer (CISO) are traditionally from the IT industry. To protect cyber-physical systems, manufacturing organisations need to have a security head who is an expert in both IT and OT.
4. Industrial Computer Emergency Response Team (CERT): Just like the proposed CertFin, a dedicated CERT for Industrial Cybersecurity can provide dedicated focus to the sector.
The world of industrial cybersecurity is evolving. Industrial cybersecurity needs to mature to the level of Information Technology security to provide a safe environment in this interconnected universe
Sagnik Chakraborty is Researcher, Cybersecurity Studies Programme.
This article is a part of Gateway House and India EXIM Bank’s study, ‘Digital Manufacturing in India‘, exclusively written for Gateway House: Indian Council on Global Relations. You can read exclusive content here.
For interview requests with the author, or for permission to republish, please contact outreach@gatewayhouse.in.
© Copyright 2021 Gateway House: Indian Council on Global Relations. All rights reserved. Any unauthorized copying or reproduction is strictly prohibited.
References:
[1] “Emergency Directive 21-01.” cyber.dhs.gov. Accessed February 10, 2021
[2] “ICS Alert (IR-ALERT-H-16-056-01).” Cybersecurity and Infrastructure Security Agency CISA. Accessed February 10, 2021
[3] “ICS-CERT MONTHLY MONITOR.” Industrial Control Systems – Cyber Emergency Response Team. U.S. Department of Homeland Security
[4] “Industrial IoT Connections to Reach 37 Billion Globally by 2025, as ‘Smart Factory’ Concept Realised.” Industrial IoT (IIoT) Connections to Reach 37bn globally by 2025. Accessed February 10, 2021.
[5] Ginter, Andrew. “THE TOP 20 CYBERATTACKS on Industrial Control Systems.” Waterfall Security Solutions LTD.
[6] “Cyber-Attack on Hydro.” Hydro.com. Accessed February 10, 2021
[7] Patil, Sameer. “India’s Vulnerable SCADA Systems.” Gateway House, December 21, 2017.
[8] Ginter, Andrew, ‘Secure Operations Technology’, (Abterra Technologies Inc. 31 December 2018)
[9] Ibid
[10] Pompon, Raymond. “Attacking Air-Gap-Segregated Computers.” F5 Labs, September 5, 2018.
[11] Ginter, Andrew, ‘Secure Operations Technology’, (Abterra Technologies Inc. 31 December 2018)
[12] Editor, CSRC Content. “Unidirectional Gateway – Glossary.” CSRC. Information Technology Laboratory. Accessed February 10, 2021.
[13] Barrett, Matthew P. “Framework for Improving Critical Infrastructure Cybersecurity Version 1.1.” NIST, January 27, 2020.
[14] Automation, International Society of. Download ISAGCA’s Quick Start Guide for the ISA/IEC 62443 Standards. Global Cybersecurity Alliance. Accessed February 10, 2021.
[15] Ibid